Enhancing AI Security: The Zero Trust Framework
Introduction
As artificial intelligence (AI) systems increasingly engage with real-time data and operational tools, the need for robust security measures becomes paramount. Researchers from Amazon Web Services (AWS) and Intuit have proposed a Zero Trust Security Framework aimed at safeguarding the Model Context Protocol (MCP) against threats such as tool poisoning and unauthorized access.
The Importance of Securing AI Interactions
AI systems are evolving to perform dynamic actions and make decisions based on live information. This evolution necessitates secure interaction channels to protect sensitive data and maintain operational integrity.
Risks Associated with AI Autonomy
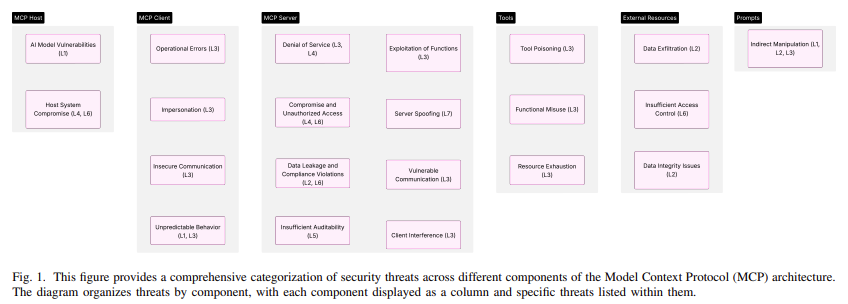
As AI systems gain autonomy, the potential for security breaches increases. Attackers may exploit vulnerabilities by manipulating tool configurations or injecting harmful instructions. This can lead to:
- Compromised operations.
- Unauthorized access to sensitive data.
- Malicious manipulation of AI model behavior.
Current Security Limitations
Traditional security frameworks, like OAuth 2.0 and Web Application Firewalls, while beneficial, do not address the unique requirements of the MCP. The MCP requires tailored defenses due to its dynamic nature, which traditional frameworks fail to accommodate.
Emerging Threats in AI Environments
Security challenges specific to MCP include:
- Prompt injection attacks.
- Schema mismatches.
- Data exfiltration risks.
The Zero Trust Security Framework for MCP
The proposed framework is designed to provide practical solutions for enterprises using MCP. Key features include:
Multi-layered Defense System
This system encompasses:
- Tool authentication.
- Network segmentation.
- Sandboxing techniques.
- Data validation processes.
Just-in-Time Access Control
Access is granted temporarily, reducing the window for potential abuse of credentials. This strategy enhances security significantly.
Behavior-Based Monitoring
Tools are monitored based on their behavior rather than just code inspection, allowing for the detection of abnormal patterns and potential threats.
Performance Metrics and Case Studies
The effectiveness of the framework is backed by performance evaluations:
- Semantic validation detected 92% of simulated poisoning attempts.
- Network segmentation reduced command-and-control channel establishment by 83%.
- Dynamic access provisioning cut the attack surface time window by over 90%.
Deployment Recommendations
Three deployment patterns are recommended:
- Isolated security zones for MCP.
- API gateway-backed deployments.
- Containerized microservices within orchestration systems like Kubernetes.
Integration with existing enterprise systems is crucial for cohesive monitoring and policy alignment.
Key Takeaways
- The MCP’s real-time AI interactions heighten security complexity.
- Tool poisoning and data exfiltration are significant risks identified.
- The framework’s strategies effectively mitigate potential threats.
- Integration with enterprise security systems ensures a comprehensive approach.
Conclusion
Implementing a tailored Zero Trust Security Framework for the Model Context Protocol offers a robust solution to the unique security challenges faced by enterprises utilizing AI technologies. By focusing on practical, structured safeguards, organizations can significantly enhance their security posture while leveraging the benefits of AI.
For guidance on effectively managing AI within your business, please reach out to us. Together, we can explore how AI technology can revolutionize your operations.




















