Understanding Ad Hoc Networks
Ad hoc networks are flexible, self-organizing networks where devices communicate without a fixed structure. They are particularly useful in areas like military operations, disaster recovery, and Internet of Things (IoT) applications. Each device functions as both a host and a router, helping to send data dynamically.
Challenges: Flooding Attacks
One major issue in these networks is flooding attacks. This happens when a malicious device sends too many fake requests or data, overwhelming the network. The result can be resource depletion, increased delays, and even network failures.
Innovative Solutions for Mitigation
Recent research has focused on several strategies to combat flooding attacks, including:
- Trust-based routing: Evaluating the trustworthiness of nodes.
- Machine learning: Using advanced algorithms to identify attacks.
- Adaptive intrusion detection: Adjusting detection methods to changing conditions.
Hybrid Routing Protocol Proposal
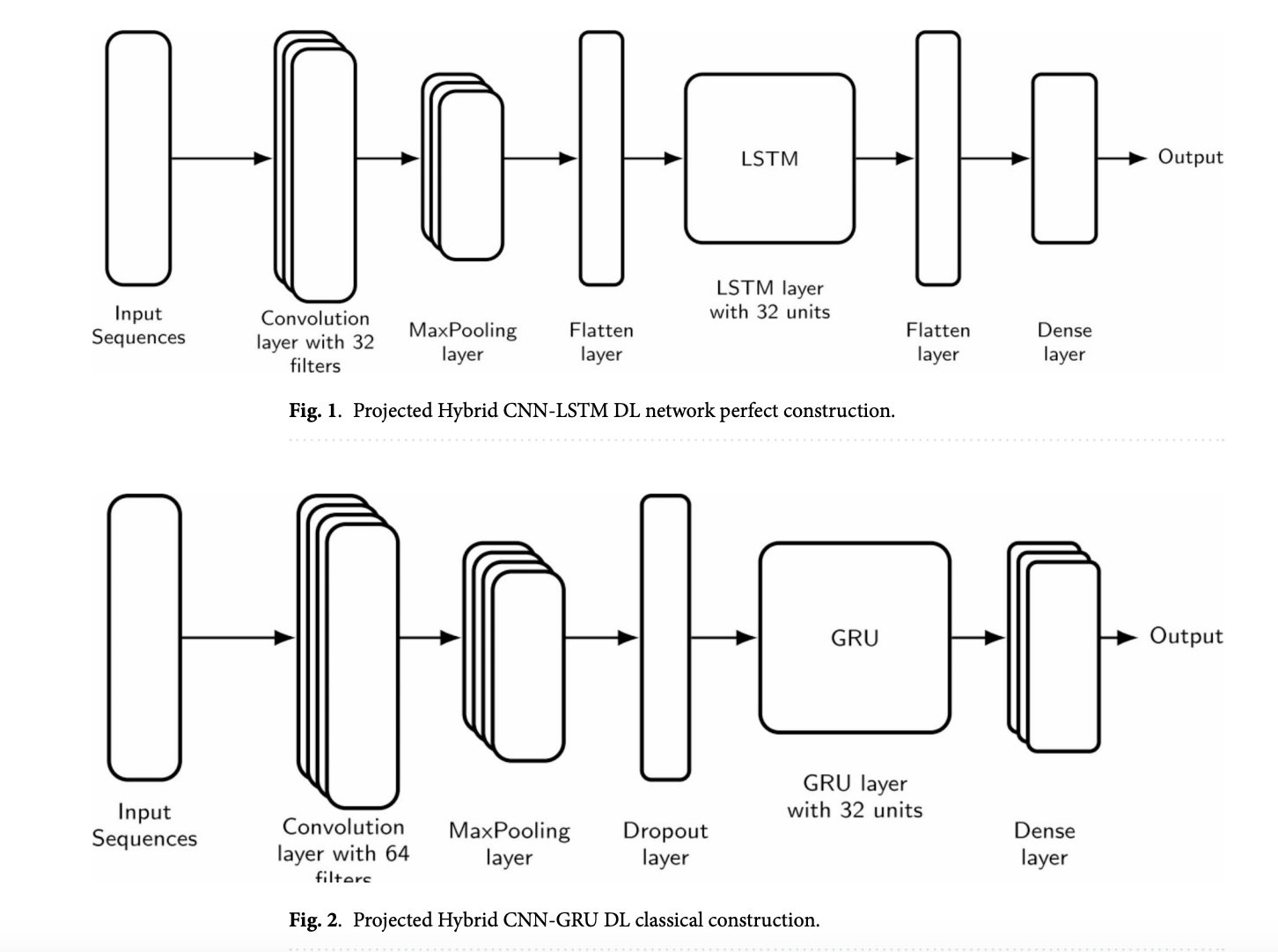
A new paper introduces an energy-efficient hybrid routing protocol designed to counter flooding attacks. This protocol uses a CNN-LSTM/GRU model for classifying nodes. It distinguishes between trusted and untrusted nodes based on their behavior, allowing for the removal of those that exceed certain limits.
How It Works
The model improves accuracy by:
- Utilizing CNN for extracting features.
- Employing LSTM or GRU for analyzing sequences.
- Optimizing decision-making in real-time.
It also conserves energy by eliminating malicious nodes when flooding attacks are detected, ensuring efficient network performance.
Performance Evaluation
The research team tested the model using MATLAB R2023a, simulating realistic conditions for accurate results. Key metrics included:
- Packet delivery ratio
- Throughput
- Routing overhead
- Stability time of cluster heads
- Attack detection time
The results showed that this new model significantly outperformed existing methods, achieving a 96.10% packet delivery ratio and 95% accuracy in classification.
Limitations and Future Directions
While promising, the model has some limitations:
- Increased complexity with larger networks.
- High memory and processing demands.
- Dependence on MATLAB simulations, which may not fully mimic real-world scenarios.
Regular updates and retraining will be essential to adapt to new attack strategies.
Conclusion
The hybrid models (CNN-LSTM and CNN-GRU) show great potential in enhancing network security but face challenges related to computational load and evolving threats.
Explore AI Solutions
If you want to enhance your company’s capabilities with AI, consider these steps:
- Identify Automation Opportunities: Find areas in customer interactions that could benefit from AI.
- Define KPIs: Ensure your AI initiatives can be measured for impact.
- Select an AI Solution: Choose tools that fit your needs and allow customization.
- Implement Gradually: Start small, gather data, and expand your AI usage wisely.
For AI management advice, reach out to us at hello@itinai.com. Stay updated on AI insights via our Telegram or @itinaicom.
Discover how AI can transform your sales and customer engagement processes at itinai.com.

























